4 Best Practices for Protecting Private Data
“Uber Fined $324 Million for Unlawful Data Transfers to the US.” Unless you’ve been off the map, you’re fully aware of the surge in data privacy regulations and compliance demand. As data breaches continue to make headlines, implementing robust data protection practices is not just a necessity but a strategic imperative. This blog post will explore four best practices organizations can adopt to safeguard private data.
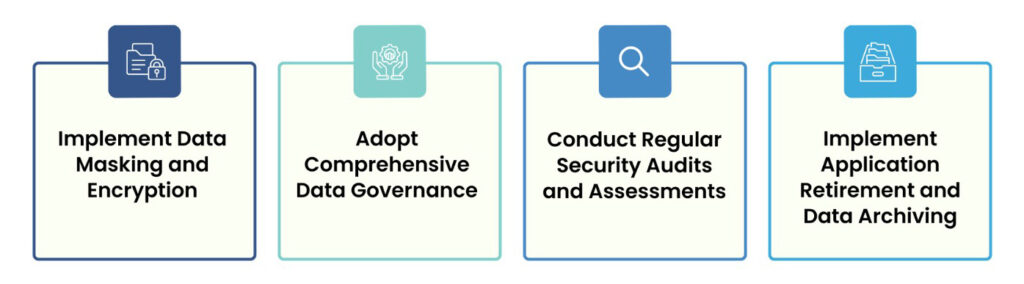
1. Implement Data Masking and Encryption
Data masking and encryption are foundational techniques to protect sensitive data from unauthorized access. Data masking obscures sensitive data with realistic but fictitious data, maintaining usability for testing and analytics while ensuring confidentiality. Encryption, on the other hand, secures data by encoding it into an unreadable format that can only be deciphered with the appropriate decryption key. By applying these techniques, organizations can mitigate the risk of data exposure both at rest and in transit.

2. Adopt Comprehensive Data Governance
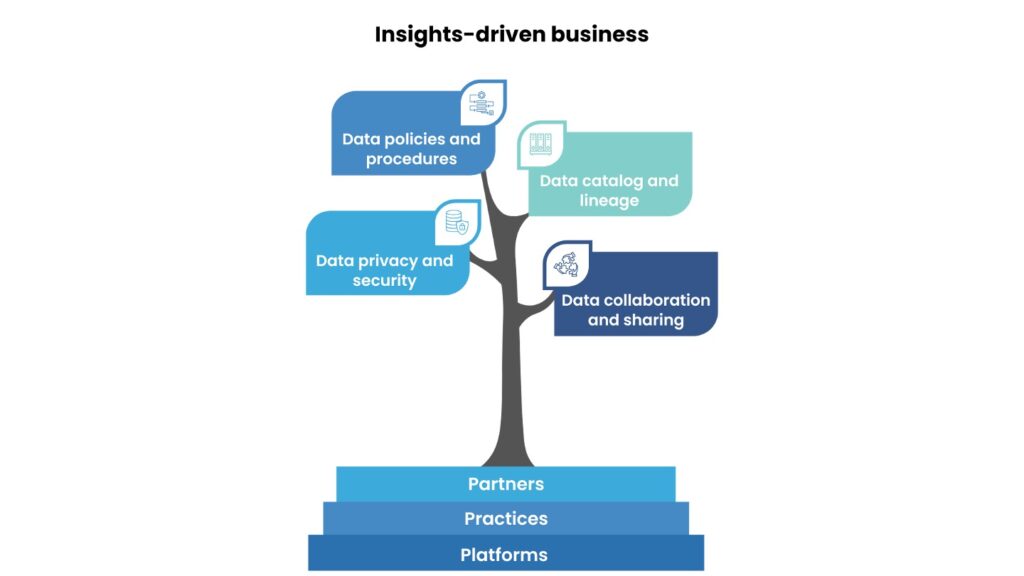
Effective data governance establishes policies, processes, and controls to manage data accessibility, integrity, and security throughout its lifecycle. By defining roles and responsibilities, implementing data classification and data quality management, conducting risk assessments, and enforcing access controls and other security measures, organizations can ensure that private data is handled responsibly and in accordance with regulatory mandates. Forrester highlights that organizations can leverage four key pillars of data governance, supported by a robust framework of partners, practices, and platforms, to drive insights and enhance business operations. (see the below figure)
3. Conduct Regular Security Audits and Assessments
Regular security audits and assessments are essential to evaluate the effectiveness of your data protection measures. Conducting comprehensive reviews of systems, networks, and applications helps identify vulnerabilities and proactively address security gaps before they are exploited. By leveraging automated tools and conducting penetration testing, organizations can continuously monitor their security posture and enhance their incident response capabilities.
4. Implement Application Retirement and Data Archiving
Application retirement and data archiving are crucial practices for managing and securing data over time. When decommissioning legacy applications, it’s essential to ensure that sensitive data is either securely deleted or archived in compliance with data retention policies. Data archiving involves storing inactive data securely and cost-effectively while maintaining accessibility for compliance and future reference. This not only helps in managing storage costs but also reduces the risk associated with data breaches involving outdated systems.
SOLIXCloud: Your Data Protection Partner
Solix CDP delivers cloud data management as-a-service for modern data-driven enterprises. Built on open source, cloud native technologies, Solix CDP helps companies manage and process all of their structured, semi-structured and unstructured data for advanced analytics, compliance, infrastructure optimization, data security, machine learning and AI.
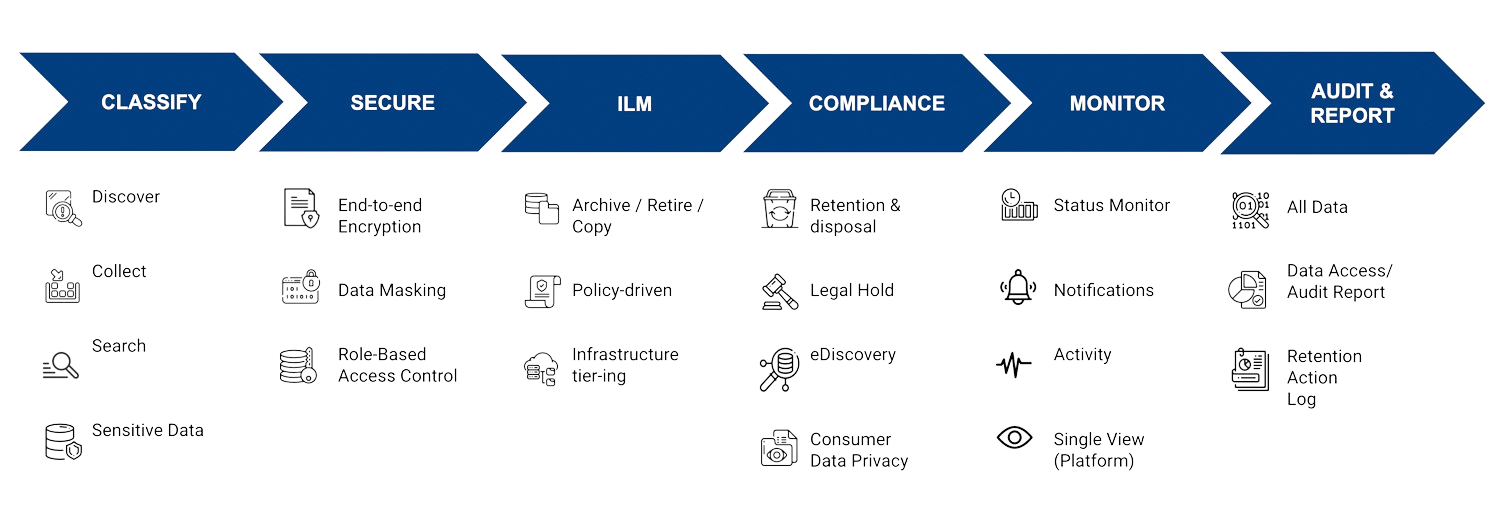
Solix Common Data Platform provides a wealth of data governance capabilities, including a business glossary, data discovery, data security, federated data governance, data classification, data access, data masking, dashboarding, role management and role-based views, workflows, approval processes, policy management, search access to your data and metadata, data profiling of both internal and external systems.
Its sensitive data discovery comes with a dedicated data privacy compliance tool that addresses GDPR, CCPA, and similar regulations; and it leverages a number of external security technologies, such as LDAP and single sign-on, as part of its data security functionality, and can integrate with a number of third party security products using these technologies.
Bottom Line
Protecting private data is a complex challenge that requires a multifaceted approach. By implementing the best practices outlined in this blog post and leveraging the expertise of trusted partners like Solix Technology, organizations can significantly reduce their risk of data breaches and safeguard their valuable assets. Schedule a demo today to learn more about what SOLIXCloud could deliver you.
Learn more: How to safeguard your data and enhance privacy in non-production and analytical environments. Download our comprehensive guide today and take the first step toward robust data protection! Read the full guide now!
Vishnu Jayan is a tech blogger and Senior Product Marketing Executive at Solix Technologies, specializing in enterprise data governance, management, security, and compliance. He earned his MBA from ICFAI Business School Hyderabad. He creates blogs, articles, ebooks, and other marketing collateral that spotlight the latest trends in data management and privacy compliance. Vishnu has a proven track record of driving leads and traffic to Solix. He is passionate about helping businesses thrive by developing positioning and messaging strategies for GTMs, conducting market research, and fostering customer engagement. His work supports Solix’s mission to provide innovative software solutions for secure and efficient data management.