Data Privacy By Design – What is it?
Blog Commentary:

As organizations amass vast amounts of personal data, the responsibility to protect this information has never been more critical. This is where the concept of “Data Privacy By Design” (DPbD) comes into play—a proactive approach that embeds privacy into the very fabric of an organization’s processes and systems from the outset.
What is Privacy By Design
Privacy-by-design or protection-by-design is a method that integrates privacy and data protection considerations into the design phase of any system, service, product, or process and continues to prioritize them throughout its entire lifecycle. Instead of treating privacy as an afterthought or a compliance checkbox, DPbD integrates privacy considerations into every stage of development.
Privacy by design framework ensures that data protection is a core design process component, ultimately leading to more secure and trustworthy products. Simply put, it is an architected approach to data management that ensures all data privacy regulations globally are met instead of requiring different solutions for different geographies and jurisdictions.
Ann Cavoukian formalized the concept of DPbD in the 1990s, and it has since been recognized as a best practice in data protection. The General Data Protection Regulation (GDPR) of the European Union even mandates DPbD, requiring organizations to implement data protection measures from the outset of any data processing activities.
The EU GDPR emphasizes the need to:
- Establish effective technical and organizational measures to uphold data protection principles
- Embed safeguards within your processing activities to ensure compliance with the EU GDPR and protect individual rights.
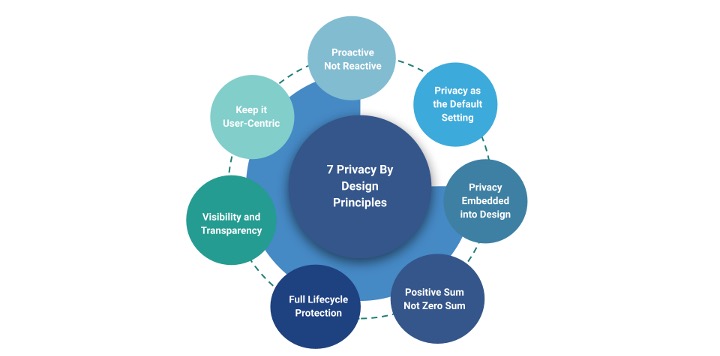
7 Privacy By Design Principles
To effectively implement DPbD, organizations should adhere to its seven foundational principles:
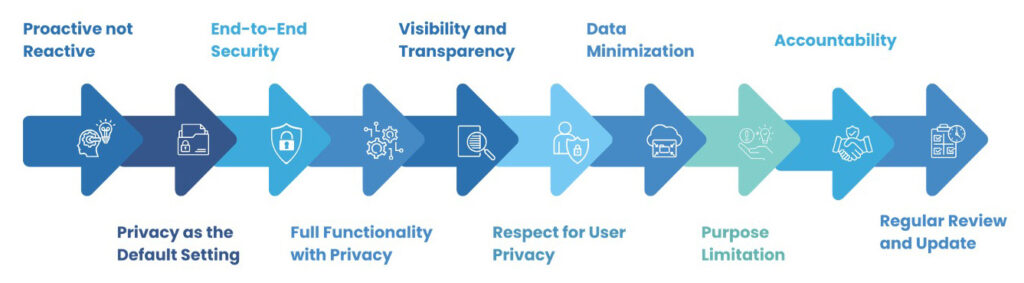
- Proactive, Not Reactive; Preventative, Not Remedial: Consider preventing privacy issues by including privacy in your designs instead of just fixing problems after they pop up.
- Privacy as the Default Setting: Systems should be privacy-centric by default, ensuring personal data is automatically protected without users taking action to secure their information.
- Privacy Embedded into Design: Privacy isn’t an add-on but a core component integrated into the design and architecture of IT systems and business practices.
- Full Functionality—Positive Sum, Not Zero Sum: Privacy by design framework advocates implementation of zero sum approach. Get privacy and security without giving up other goals or functionalities, ensuring a win-win scenario.
- End-to-End Security—Full Lifecycle Protection: Data privacy measures should protect data throughout its entire lifecycle, from collection to deletion.
- Visibility and Transparency—Keep it Open: Organizations should be transparent about data practices, providing clear and accessible information to build trust and accountability.
- Respect for User Privacy—Keep it User-Centric: Organizations should prioritize user needs by giving them control over their data and respecting their privacy preferences.
Why Should We Care About Privacy By Design?
The importance of DPbD cannot be overstated. DPbD offers a framework that not only safeguards data but also enhances an organization’s reputation, fosters customer trust, and ensures compliance with privacy regulations.
- Compliance Regulations: DPbD helps organizations meet legal obligations under laws like GDPR, CCPA, etc, avoiding fines and reputational damage.
- Enhanced Trust and Reputation: Prioritizing data privacy builds customer trust, a key differentiator in today’s competitive market.
- Mitigation of Privacy Risks: Embedding privacy into design helps identify and mitigate risks, reducing the likelihood and cost of data breaches.
- Competitive Advantage: DPbD offers a competitive edge by attracting and retaining privacy-conscious customers.
Privacy By Design Checklist
Privacy by Design checklist is a set of guidelines that helps organizations embed privacy into their processes, safeguarding user data by default and throughout its entire lifecycle. Below are a few privacy-by-design examples:
How to Implement Privacy By Design
For DPOs and compliance officers, effectively understanding and implementing this approach is key to mitigating risks and achieving compliance with evolving data protection regulations. To effectively implement DPbD, organizations should take the following steps:
- Conduct a Privacy Impact Assessment (PIA): Identify and mitigate privacy risks early in new projects or systems.
- Integrate Privacy into the Development Process: Ensure privacy is considered at every stage, from concept to deployment.
- Privacy By Design Training: Regularly train employees on the importance of data privacy and their role in maintaining it.
- Leverage Privacy-Enhancing Technologies (PETs): Protect personal data with tools like data masking, encryption, and anonymization.
- Foster a Culture of Privacy: Encourage a privacy-centric culture with leadership support and clear communication of privacy policies by encouraging employees to take ownership of privacy in their daily work.
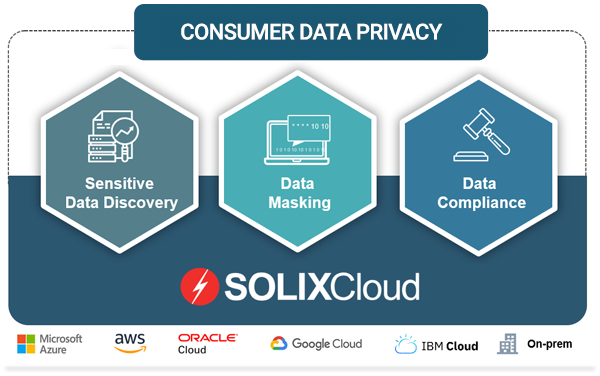
SOLIXCloud Privacy By Design
SOLIXCloud Consumer Data Privacy is a suite of integrated solutions to help SOLIXCloud Common Data Platform (CDP) customers meet the growing requirements for consumer data protection. The “privacy by design” suite of solutions includes end-to-end encryption, metadata management, data profiling, data governance rules, sensitive data discovery, data masking, and data compliance to ensure all personally identifiable information (PII) is properly identified, classified, masked and able to meet regulatory requirements including GDPR, CCPA, NYDFS, LGPD, PII, PHI and PCI.
Privacy by design approach must be adopted as it is not just a regulatory requirement but a strategic approach that can benefit organizations in multiple ways. Take the first step towards securing sensitive information in your organization by downloading our ebook, “From Detection to Protection: The Essentials of Sensitive Data Discovery and Security-Compliance Tools.”
Vishnu Jayan is a tech blogger and Senior Product Marketing Executive at Solix Technologies, specializing in enterprise data governance, management, security, and compliance. He earned his MBA from ICFAI Business School Hyderabad. He creates blogs, articles, ebooks, and other marketing collateral that spotlight the latest trends in data management and privacy compliance. Vishnu has a proven track record of driving leads and traffic to Solix. He is passionate about helping businesses thrive by developing positioning and messaging strategies for GTMs, conducting market research, and fostering customer engagement. His work supports Solix’s mission to provide innovative software solutions for secure and efficient data management.