
Eight Data Subject Rights
Blog Commentary:

As organizations continue to collect and process vast amounts of personal data, data subject rights have become a cornerstone of modern privacy legislation. These rights are designed to give individuals control over their personal information and hold organizations accountable for handling data. Whether your company works with customer data or manages enterprise systems, understanding data subject rights is critical for maintaining compliance and fostering stakeholder trust.
Numerous regulations are now in place across different geographies, including the General Data Protection Regulation (GDPR) in the EU, California Consumer Privacy Act (CCPA), Virginia’s Consumer Data Privacy Act (CDPA), New York’s Department of Financial Services Cybersecurity Regulation (NYDFS), Brazil’s Lei Geral de Proteção de Dados Pessoais and others. According to the United Nations Trade and Development (UNCTAD), 137 out of 194 countries have implemented legislation to secure data protection and privacy.

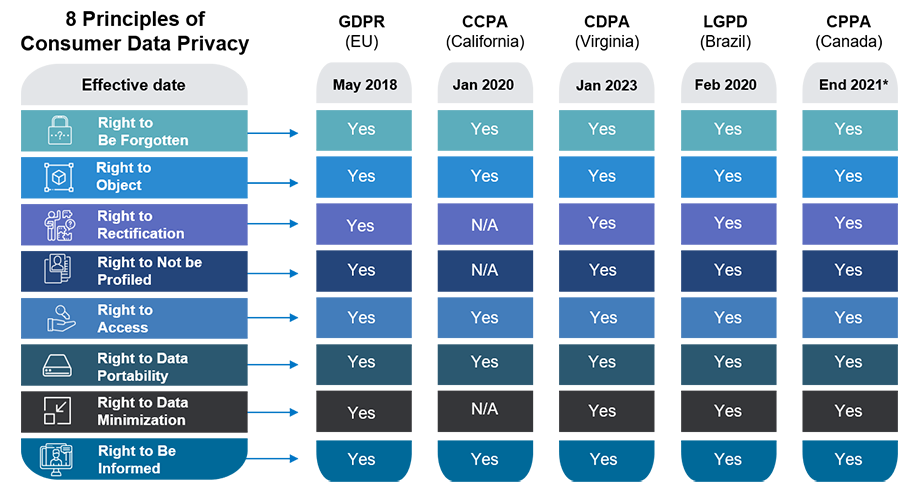
Right to be Forgotten
GDPR defines the Right to be Forgotten or Erasure as – “The data subject has the right to request the erasure of their personal data without undue delay, and the controller must comply if the data is no longer necessary, consent is withdrawn, an objection is made, the data was unlawfully processed, or erasure is required for legal compliance”.
This seemingly straightforward requirement is, in fact, quite complex, as organizations must first be able to locate the requested data within silos of enterprise data or even hidden as orphaned objects within database tables. This is where sensitive data discovery tools come to the rescue, easing the process of extracting the required sensitive data from siloed enterprise databases.
Right to Rectification
GDPR defines the Right to Rectification as: “The data subject shall have the right to obtain from the controller without undue delay the rectification of inaccurate personal data concerning him or her.” This right not only enhances individual control over personal data but also helps organizations maintain data integrity.
A comprehensive search and discovery capability is once again an essential capability for data processors, but since the rectification process also requires that data be updated, processors require role-based access control to limit privileged access to sensitive personal information.
Right to Object
The Right to Object empowers individuals to request that data processors stop processing their personal data at any time. Even if data is processed based on legitimate interests, individuals can object to such processing.
The right to object includes opt-in and opt-out methods for consumers to voice their concerns about how their data is being used for processing. Metadata management and data catalogs improve visibility and control for controllers and data processors to search multi-cloud landscapes for all instances of the data and remove it from processing.
Right to Data Minimization
The right to Restrict Processing or Data Minimization ensures that controllers and data processors limit the collection and processing of personal data to only what is necessary. This right ensures that data collection is relevant and sufficient to fulfill the stated purpose.
Metadata management and data catalogs help administrators explore their data landscape to confirm the scope of data to be processed, and Information Lifecycle Management (ILM) provides data retention policies to ensure that the data is purged (deleted) once it is no longer needed.
Right to Data Portability
The data subject has the right to receive their personal data, provided to a controller, in a structured, commonly used, and machine-readable format. They also have the right to transmit this data to another controller without hindrance, provided the processing is based on consent or a contract and is carried out by automated means.
As organizations store more data in multi-cloud environments, the World Wide Web Consortium (W3C) has introduced open-source data management standards to enhance interoperability. Without data portability, personal data is restricted to the platform on which it’s stored. W3C’s cloud-native architecture solves this by storing data in standard formats, making it easily accessible across different platforms.
Right to be Informed
The right to be informed assures that consumers are informed about the personal data collected and how the data will be processed, including retention periods and disclosure of any data-sharing agreements.
Organizations that collect personal data directly from individuals can inform them about its use. When data comes from third-party sources, they still must notify individuals. This can be achieved through layering, dashboards, and timely notifications (emails or alerts) within one month of the data collection.
Right to not be Profiled
In an era where artificial intelligence and machine learning are used to automate decisions, this right ensures individuals are not subject to decisions made solely by automated processes that significantly affect them, such as loan approvals or credit scoring. Organizations must implement safeguards and offer human intervention where necessary to mitigate risks of bias or unfair outcomes.
Right to Access
The Right to Access involves data processors giving individuals access to their personal data stored in their systems. For example, an individual may submit a Subject Rights Requests (SRR) form to obtain information about their personal data.
This includes information about how their data is processed, the categories of data involved, and any third parties that have received their data. Organizations are required to respond to such requests promptly, typically within one month, allowing individuals to verify the accuracy of their data and understand its use.
SOLIXCloud Consumer Data Privacy
Data privacy by design is an architected approach to cloud data management that ensures all data privacy regulations globally are met instead of requiring different solutions for different geographies and jurisdictions.
SOLIXCloud Consumer Data Privacy is a suite of three powerful tools that complement the W3C open standards-based security, SOLIXCloud Common Data Platform, and the Eight Principles of Consumer Data Privacy.
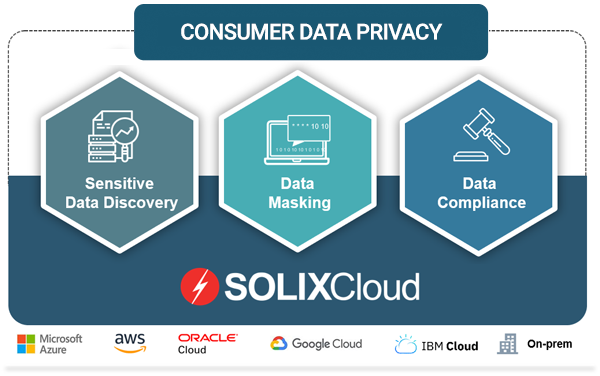
Solix Sensitive Data Discovery: Solix Sensitive Data Discovery offers an expansive suite for identifying sensitive information across hundreds of data sources across On-prem and Cloud environments and spanning structured and unstructured data types. With prebuilt discovery patterns and the flexibility to incorporate custom patterns, identifying sensitive data across the enterprise landscape is now easy and efficient. This holistic solution also provides comprehensive reports, ensuring robust compliance and audit readiness for organizations.
Solix Data Masking: Solix Data Masking offers a comprehensive multi-cloud solution to safeguard sensitive data across diverse data repositories and types. It encompasses a range of masking techniques, such as referential masking, redaction, format-preserving encryption, and more. Users can leverage its pre-defined security rules or introduce custom rules. By preserving format and referential integrity across datasets, Solix ensures that the data remains functional without compromising compliance or data security standards.
Solix Data Compliance: SOLIXCloud Consumer Data Privacy is a suite of integrated solutions to help SOLIXCloud Common Data Platform (CDP) customers meet the growing requirements for consumer data protection. The “privacy by design” suite of solutions includes end-to-end encryption, metadata management, data profiling, data governance rules, sensitive data discovery, data masking, and data compliance to ensure all personally identifiable information (PII) is properly identified, classified, masked and able to meet regulatory requirements including GDPR, CCPA, NYDFS, LGPD, PII, PHI and PCI.
Learn more: “How to Comply with Consumer Data Privacy Regulations?” The full guide offers actionable steps to ensure compliance with consumer data privacy regulations and protect your business from costly violations. Read it now!
Vishnu Jayan is a tech blogger and Senior Product Marketing Executive at Solix Technologies, specializing in enterprise data governance, management, security, and compliance. He earned his MBA from ICFAI Business School Hyderabad. He creates blogs, articles, ebooks, and other marketing collateral that spotlight the latest trends in data management and privacy compliance. Vishnu has a proven track record of driving leads and traffic to Solix. He is passionate about helping businesses thrive by developing positioning and messaging strategies for GTMs, conducting market research, and fostering customer engagement. His work supports Solix’s mission to provide innovative software solutions for secure and efficient data management.




