Data Leakage Protection – Closing the Gaps
As enterprise data grows in size and importance, organizations are facing a critical fight to stem flow of sensitive information beyond corporate boundaries. While security teams concentrate on defending against external cyber threats, confidential data may be quietly slipping through digital cracks, often through completely legitimate and seemingly innocent channels.
Listen to the Blog

The Rising Cost of Data Exposure
The financial implications are sobering. Industry analysis shows that the average cost of unauthorized data exposure has reached $4.35 million in 2023, with regulated industries facing even steeper penalties. Beyond immediate financial losses, organizations must contend with long-term consequences: damaged reputation, erosion of customer trust, and regulatory sanctions that can impact operations for years.
Modern Approaches to Data Protection
Contemporary data protection solutions have evolved far beyond simple pattern matching and basic filtering. Today’s enterprise-grade systems employ sophisticated algorithms that analyze content, context, and user behavior patterns to identify and prevent unauthorized data movement. These advanced platforms can distinguish between routine business communications and potentially risky data transfers that require intervention.
The most effective solutions combine several critical components: data discovery and classification, automated policy enforcement, encryption management, and comprehensive audit trails. Modern platforms also provide real-time monitoring capabilities and seamless integration with cloud services where sensitive information increasingly resides.
Enterprise-Wide Data Security Framework
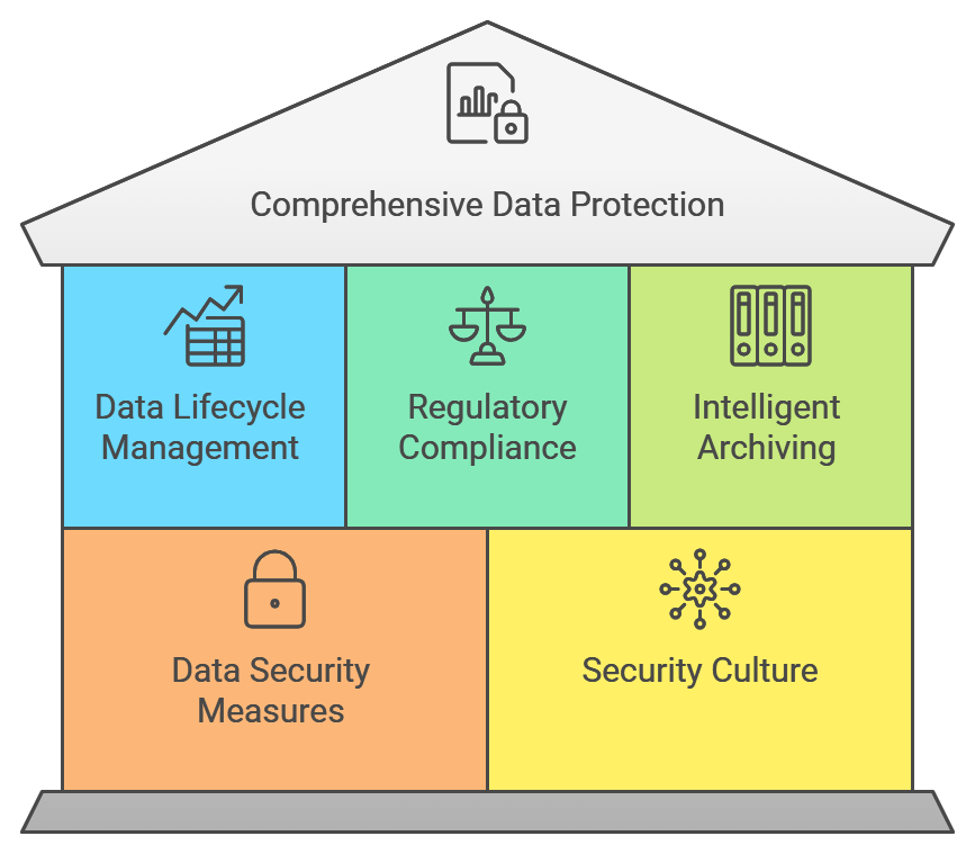
Leading enterprise data security platforms now offer comprehensive solutions that address the entire data lifecycle. These systems begin with automatic discovery and classification of sensitive information across databases, file systems, and cloud storage (Sensitive Data Discovery Made Easy | Identify PII, PHI, and more). They then apply intelligent archiving strategies, ensuring that data remains accessible while maintaining strict security protocols.
Advanced data masking capabilities protect sensitive information during development and testing phases, while robust access controls ensure that only authorized personnel can view or modify critical data. These systems also provide sophisticated tools for managing data retention policies and implementing defensible deletion strategies when data reaches the end of its lifecycle.
Regulatory Compliance and Risk Management
Modern enterprises must navigate an increasingly complex regulatory landscape, including GDPR, CCPA, HIPAA, and industry-specific requirements. Contemporary data protection platforms provide built-in compliance frameworks that automatically apply appropriate security controls based on data classification and regulatory requirements.
These systems maintain detailed audit trails and generate compliance reports that demonstrate due diligence to regulators. They also provide tools for conducting regular risk assessments and implementing appropriate controls based on the sensitivity of different data categories.
The Role of Enterprise Data Archiving
A crucial component of comprehensive data protection is intelligent archiving. Modern solutions employ sophisticated archiving strategies that balance security, accessibility, and cost-effectiveness. By implementing tiered storage architectures, organizations can maintain appropriate security controls while optimizing storage costs and ensuring rapid data retrieval when needed. SOLIXCloud Enterprise Data Archiving Solution | Manage Growth
Protecting Data in Motion and at Rest
Effective data protection requires securing information throughout its lifecycle. This includes protecting data in transit between systems, at rest in storage, and during use in applications. Modern solutions employ end-to-end encryption, secure communication protocols, and granular access controls to maintain security across all states of data existence.
Creating a Culture of Data Security
While technological solutions are crucial, successful data protection requires fostering a culture of security awareness throughout the organization. This involves regular training programs, clear policies, and establishing processes that make secure data handling an integral part of daily operations rather than an afterthought.
The Path Forward
Organizations looking to enhance their data protection strategies should begin with a comprehensive assessment of their current data landscape. This includes identifying sensitive data locations, understanding data flows, and evaluating existing security controls. Based on this assessment, organizations can implement appropriate technical controls while developing clear policies and training programs.
Success in data protection requires ongoing vigilance and regular updates to security measures as threats evolve and new vulnerabilities emerge. It’s not just about implementing technology—it’s about creating a comprehensive framework that addresses people, processes, and technology in equal measure.
This issue is cross-organizational, protecting sensitive data isn’t merely an IT concern—it’s a fundamental business imperative that requires attention from every level of the organization. Those who fail to implement comprehensive data protection measures risk not just financial losses, but their very survival in an era mandating data protection.
Stephen Tallant
As the Director of Product Marketing at Solix Technologies, I lead the development and communication of the product and solution story to the market. I have over 25 years of experience in product marketing and product management, creating engaging messaging, launch plans, collateral, and content for various software solutions. I live in metro Philadelphia, and am a big sports fan - so much so, I sit on the Board of the Philadelphia Sports Hall of Fame. I attended Villanova University for both my undergraduate and graduate degrees.