Privacy Impact Analysis For Large Cloud Deployments
As organizations increasingly migrate their operations to the cloud, ensuring the privacy and security of sensitive data becomes paramount. A Privacy Impact Analysis (PIA) is a critical process that helps organizations identify, assess, and mitigate potential privacy risks associated with large cloud deployments. This blog explores the significance of conducting a PIA, the steps involved, and its implications for compliance with evolving data protection regulations.
What is Privacy Impact Analysis?
A Privacy Impact Analysis (PIA) systematically evaluates how personal data is collected, used, stored, and shared in a cloud environment to protect personally identifiable information (PII) from unauthorized access and breaches. PIAs identify privacy risks during a system’s development lifecycle, helping organizations understand data management practices and ensure compliance with relevant legal frameworks.
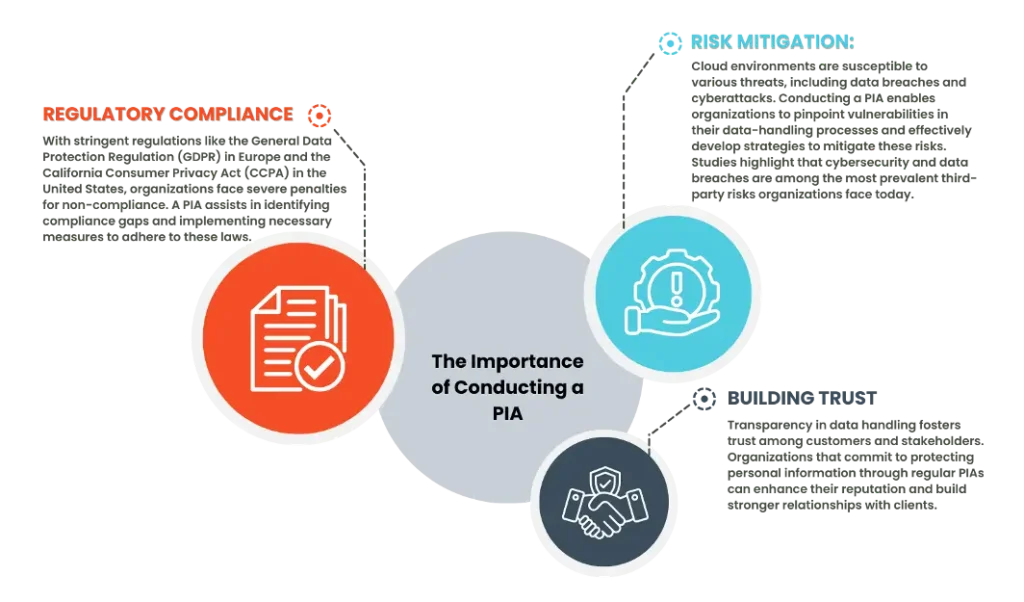
The Importance of Conducting a PIA
According to Gartner, by the end of 2025, 85% of enterprises will be “cloud-first,” and 95% of digital workloads will be deployed on cloud-native platforms. This massive shift underscores the importance of robust privacy assessment frameworks. The following are a few reasons why PIAs are of great importance for enterprises.
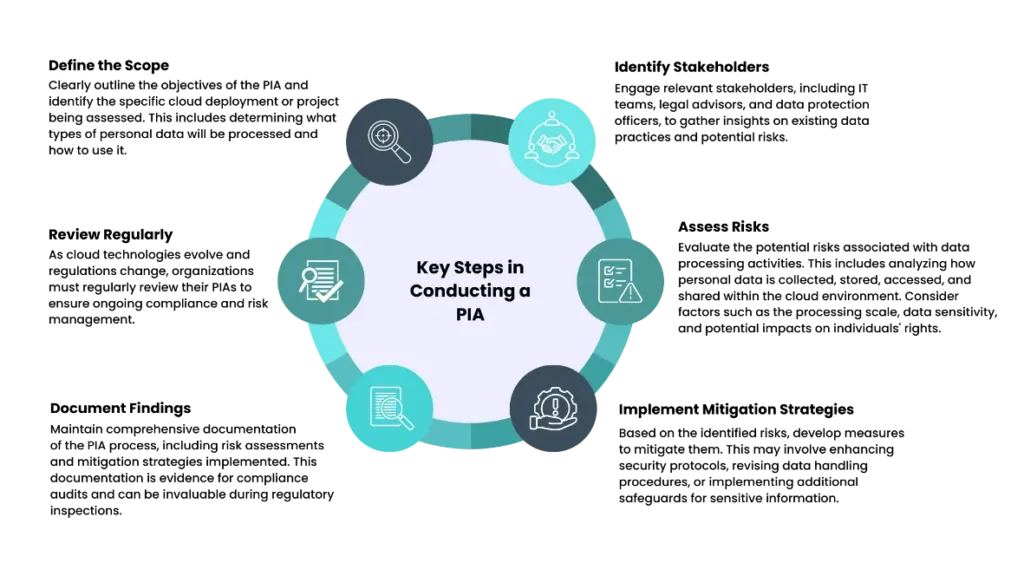
Key Steps in Conducting a PIA
By performing a PIA, organizations can assess how personal data is collected, stored, used, and shared and determine the necessary safeguards to prevent privacy issues before they arise. This assessment is particularly important in an era of increasing privacy regulations, where compliance is not only a legal obligation but a vital aspect of corporate reputation. These key steps, from defining the scope and identifying stakeholders to assessing risks and implementing mitigation strategies, will help ensure compliance and protect individual privacy rights.
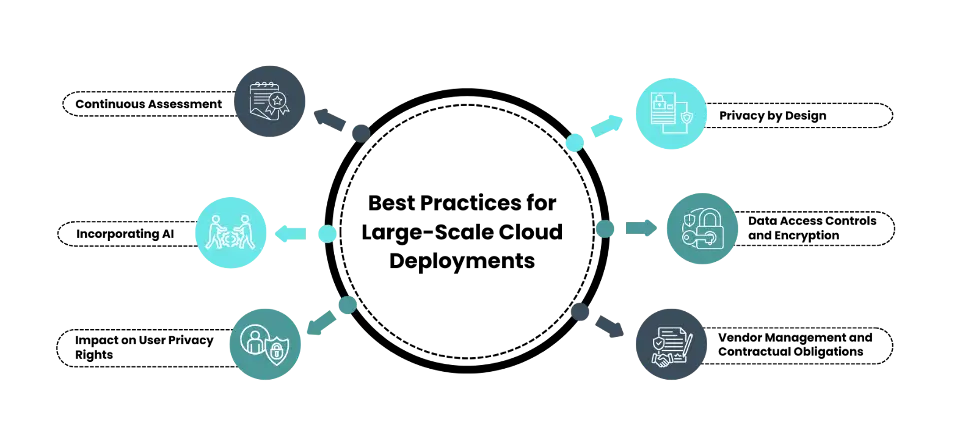
Best Practices for Large-Scale Cloud Deployments
As enterprises turn to large-scale cloud deployments widely, ensuring robust privacy protections is not just a compliance requirement but a strategic imperative. Adopting best practices becomes crucial as organizations navigate the complexities of dynamic cloud environments.
- Continuous Assessment: Privacy impact analysis should be an ongoing process rather than a one-time exercise. The dynamic nature of cloud environments requires regular reassessment of privacy controls and risks.
- Privacy by Design: Incorporate privacy considerations from the earliest stages of cloud deployment planning. Studies report that organizations implementing Privacy by Design principles experience 50% fewer privacy breaches.
- Incorporating AI: Leverage AI and machine learning to improve privacy impact analysis for large cloud deployments through automated monitoring, anomaly detection, and data classification, proactively addressing privacy risks.
- Data Access Controls and Encryption: PIA should encompass an evaluation of access management, encryption protocols, and data isolation to mitigate risks of unauthorized access and data breaches.
- Impact on User Privacy Rights: To protect individual privacy rights, organizations must carefully assess and implement measures to address the privacy impact of large cloud deployments, including data sharing, transfer, and processing.
- Vendor Management and Contractual Obligations: For organizations using third-party cloud services, effective vendor management is vital for data protection across the supply chain. It requires metrics to evaluate compliance, incident response times, and security incident notifications for transparency and accountability.
Metrics for Effective PIAs
Below are key metrics to measure the effectiveness of PIAs, ensuring comprehensive risk management and compliance.:
- Number of Identified Risks: Monitor how many privacy risks were identified during each assessment.
- Mitigation Implementation Rate: Track the percentage of identified risks successfully mitigated.
- Compliance Audit Results: Assess outcomes from external audits related to privacy practices.
- Stakeholder Engagement Levels: Evaluate participation from relevant stakeholders during the PIA process.
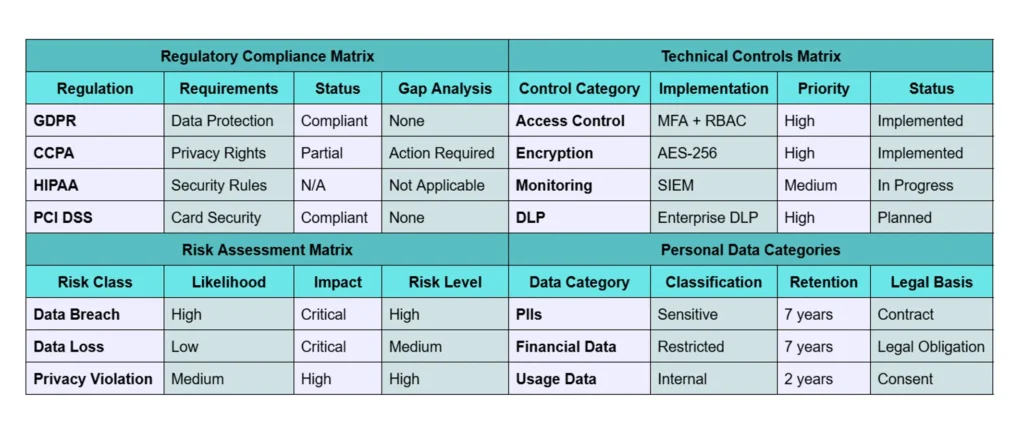
Apart from those mentioned above, many metrics could be used to evaluate a PIA analysis. The table below illustrates a hypothetical PIA analysis result of XYZ enterprise.
Bottom Line
As organizations grow their cloud presence, conducting thorough privacy impact analyses (PIAs) becomes essential. A well-executed PIA safeguards sensitive data, fosters trust among stakeholders, and ensures compliance with regulations. Organizations can effectively manage the complexities of large-scale cloud deployments by adopting a structured approach and implementing strong privacy measures while upholding high privacy standards.
Learn more: “How to Comply with Consumer Data Privacy Regulations?” The full guide offers actionable steps to ensure compliance with consumer data privacy regulations and protect your business from costly violations. Read it now!
Vishnu Jayan is a tech blogger and Senior Product Marketing Executive at Solix Technologies, specializing in enterprise data governance, management, security, and compliance. He earned his MBA from ICFAI Business School Hyderabad. He creates blogs, articles, ebooks, and other marketing collateral that spotlight the latest trends in data management and privacy compliance. Vishnu has a proven track record of driving leads and traffic to Solix. He is passionate about helping businesses thrive by developing positioning and messaging strategies for GTMs, conducting market research, and fostering customer engagement. His work supports Solix’s mission to provide innovative software solutions for secure and efficient data management.