The Role of Data Masking in Achieving Zero Trust Security
Blog Commentary:

By the end of 2025, 60% of organizations will adopt Zero Trust as a foundational security model, yet only half will achieve measurable outcomes, warns Gartner. This gap underscores the urgency for strategies that operationalize zero-trust principles effectively. Among these, Data Masking emerges as a critical enabler—transforming how enterprises secure sensitive information while maintaining usability. For CISOs and CTOs navigating escalating cyber threats and regulatory demands, integrating data masking into Zero Trust architectures isn’t optional; it’s imperative. This blog explores how masking fortifies data security, mitigates insider risks, and aligns with global compliance mandates.
What is Zero Trust Security?
Security breaches have escalated to alarming levels, with 83% of organizations experiencing multiple data breaches in 2023, according to a leading industry report on the cost of data breaches. As perimeter-based security continues to fail, zero-trust architecture has emerged as the gold standard for enterprise security frameworks. Within this architecture, data masking stands as a critical component that many security leaders overlook.
Zero Trust security is built on the principle of “never trust and always verify,” where every user, device, and network interaction is treated as untrusted until proven otherwise. This model is particularly relevant in hybrid work environments, where traditional perimeter-based security models are ineffective against sophisticated cyber threats. Zero Trust emphasizes continuous monitoring, multi-factor authentication, and micro-segmentation to limit user access and prevent breaches. The core pillars of Zero Trust include:
- Identity and access management (IAM): Ensures users are who they claim to be.
- Least privilege access: Grants only the minimum required access.
- Micro-segmentation: Restricts lateral movement within the network.
- Data protection: Encrypts and masks sensitive information.
- Continuous monitoring: Detects and responds to anomalies in real time.
Synergy Between Data Masking and Zero Trust
Zero Trust operates on a “never trust, always verify” ethos, requiring continuous validation of user access and strict least-privilege controls. Data masking complements this by de-identifying sensitive data, ensuring that even if attackers bypass perimeter defenses, the information they access holds no exploitable value. When integrated with zero-trust architectures, data masking ensures that only authorized personnel can access unmasked data, adhering to the principle of least privilege access.
Consider non-production environments, where real data is often used for testing. A 2023 Ponemon Institute study found that 63% of data breaches originated from internal errors or misuse. Masking production data in these environments reduces exposure, ensuring developers interact only with anonymized datasets.
How Data Masking Advances Zero Trust Principles
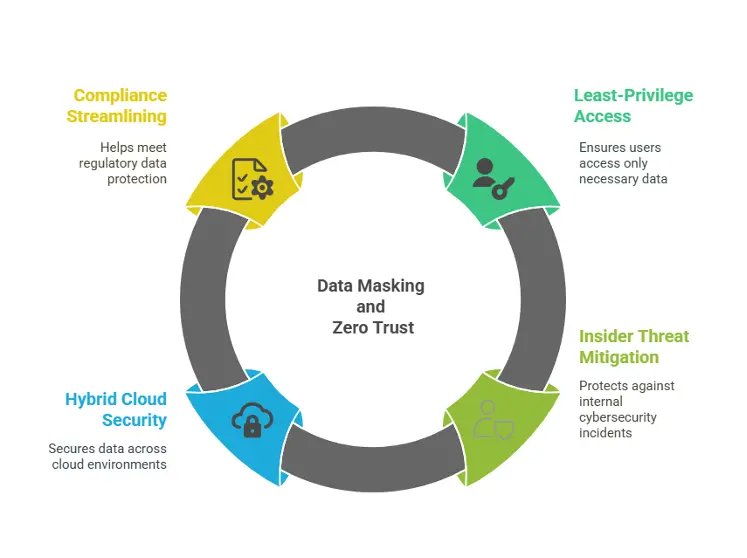
- Least-Privilege Access Reinforced: Zero Trust mandates granting minimal access necessary for tasks. Data masking adds a layer of defense by altering sensitive fields (e.g., credit card numbers, Social Security IDs) into realistic but fictitious values. This ensures that even authorized users see only what they need. For example, a customer support representative may only see masked credit card numbers, while a finance officer may have access to the full data set.
- Mitigating Insider Threats: According to the 2023 Cost of Insider Risks Report, insider threats account for 60% of cybersecurity incidents. Dynamic masking applies masking rules on the fly as data is accessed based on user context and privileges. This allows security leaders to implement just-in-time, least-privilege access to sensitive data—a core principle of zero-trust architecture.
- Securing Hybrid Cloud Ecosystems: As organizations migrate data to the cloud, visibility gaps grow. Masking structured and unstructured data at rest, in transit, or during processing ensures consistency across hybrid environments—a core tenet of Zero Trust. Masking techniques, such as tokenization and dynamic data masking, help organizations maintain security without disrupting workflows.
- Streamlining Compliance: Regulations like GDPR and CCPA impose strict rules on data handling. Masking simplifies compliance by reducing the scope of sensitive data exposure. Forrester notes, “Proactive data anonymization cuts audit preparation time by 40% while minimizing breach penalties.”
Integrating Data Masking into Zero Trust Architecture
For CISOs and CTOs, integrating data masking into Zero Trust frameworks requires a phased approach:
- Inventory Sensitive Data: Identify where regulated or critical data resides—databases, cloud storage, and legacy systems.
- Map Data Flows: Understand how data moves across systems to apply masking at optimal points (e.g., during ingestion or replication).
- Integrate with IAM: Align masking policies with identity and access management (IAM) systems to automate role-based data obfuscation.
- Automate in DevOps: Embed masking into CI/CD pipelines to secure test environments without slowing development cycles.
- Monitor Continuously: Use analytics to detect unmasked data leaks and refine policies.
Data masking doesn’t just protect; it future-proofs. With 68% of business leaders citing data privacy laws as a top operational challenge (IDC, 2023), masking ensures archived or retired application data remains compliant. For example, when decommissioning legacy systems, masking preserves data utility for audits without exposing raw sensitive details.
As organizations continue their zero-trust journeys, data masking serves as a crucial yet often overlooked component. For Data Guardians, the message is clear: comprehensive zero trust requires protection at the data layer. By implementing robust data masking as part of your security architecture, you create a resilient security posture that protects what matters most—your data—regardless of where it resides or how it’s accessed. Masking isn’t a siloed tool—it’s the backbone of resilient Zero Trust architectures.
Data Masking ebook:
Learn more: How to safeguard your data and enhance privacy in non-production and analytical environments. Download our comprehensive guide today, “ A Guide to Data Security and Data Privacy in Non-Production and Analytical Environments,” and take the first step toward robust data protection! Read the ebook now!
Vishnu Jayan is a tech blogger and Senior Product Marketing Executive at Solix Technologies, specializing in enterprise data governance, management, security, and compliance. He earned his MBA from ICFAI Business School Hyderabad. He creates blogs, articles, ebooks, and other marketing collateral that spotlight the latest trends in data management and privacy compliance. Vishnu has a proven track record of driving leads and traffic to Solix. He is passionate about helping businesses thrive by developing positioning and messaging strategies for GTMs, conducting market research, and fostering customer engagement. His work supports Solix’s mission to provide innovative software solutions for secure and efficient data management.