No Excuse for Non-Production Database Breaches
Solix EDMS Data Masking Standard Edition (SE) Comments Off on No Excuse for Non-Production Database BreachesPrivacy.org reports that over 500 million credit card records have been breached since 2005. Say what? 500 million?
Last week it was reported that 400,000 clear text passwords were breached from Yahoo within a day. Yahoo spokeswoman Dana Lengkeek said "an older file" had been stolen. Such a breach suggests Yahoo did not mask their Non-production data.
Who cares? Well, Trusted ID reports an identity is stolen every 4 seconds and there are over 10 million identity theft victims in the US. Furthermore, the average cost to restore a stolen identity is $8,000, and victims spend an average of 600 hours recovering from this crime.
The fact is that too many organizations still have not taken adequate steps to protect Non-production data and comply with the Payment Card Industry Data Security Standard (PCI DSS). Non-production databases often store sensitive data cloned from production, and this data is often left unprotected on development servers, laptops and test instances. PCI DSS Requirement 3.4 mandates that stored cardholder data is protected “anywhere it is stored,” yet somehow, non-production databases are often overlooked in security plans.
Data must be protected where it lives – in the database, and it is not surprising so many attacks target non-production databases. Non-production data is a soft target since there is a lot more of it and fewer controls are in place. Furthermore, high profile thefts reveal that insiders often do most of the damage. Sometimes the culprit is a disgruntled employee, but more often sensitive test data inadvertently ends up on a stolen laptop, is lost through outsourcing, or simply gets misplaced on account of weak or nonexistent controls.
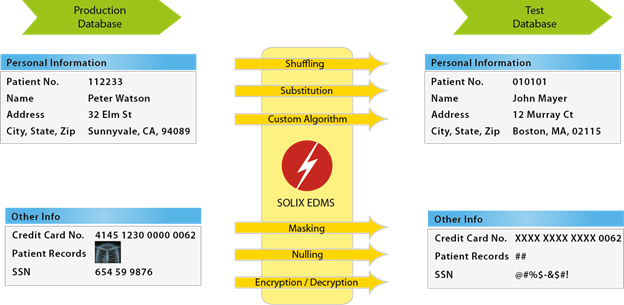
Data masking has emerged as a best practice to protect non-production data because unlike encryption, masking is able to support the entire application development lifecycle. Data masking removes personally identifiable information such as a person’s name and account, credit card, or social security number, and transforms it into contextually accurate, albeit fictionalized, data. By obfuscating the information, data masking de-identifies personally identifiable information. And because it is no longer confidential, masked data is acceptable for use in nonproduction environments such as application development.
The Data Masking Process
But even despite best practices, many companies still do not mask non-production data. One problem is that “small and mid-sized companies don’t have dedicated security staff to manage complicated security systems. For products to help small companies they’ve got to be dead simple to use, automate basic security functions and save them time. The product has to make their jobs easier, not be their job,” according to Adrian Lane, CTO at Securosis.
In the absence of an existing control process or tools to mask sensitive data, database administrators must create and maintain scripts. But it makes little sense to build and maintain a masking tool set in house while so many other priorities exist for scarce DBA resources. Furthermore, enterprise IT organizations must demonstrate the ability to mask data consistently across all application environments. Compliance objectives require a clear and consistent process.
To the relief of many, free database security software tools are finally making an overdue market entrance. MySQL audit plugins, free vulnerability scanners, and now, free data masking solutions are widely available. Even more important, these free downloads are designed from the ground up to deploy fast and be easy to use.
Certain free software tools may impose vendor restrictions on deployment and usage, but free database security software still represents a better, faster, cheaper way to get started protecting non-production data. So, there really is no excuse for a non-production database breach!
Editorial Note: This week Solix released Solix EDMS Data Masking Standard Edition, a free download enabling sensitive data to be masked across non-production instances of enterprise applications. The software may be downloaded and fully deployed in minutes through an easy to use four step deployment wizard. http://www.solix.com/products/solix-enterprise-standard-edition/
I http://breachalerts.trustedid.com/category/employee-data/page/2/
II Pescatore, John. “High-Profile Thefts Show Insiders Do the Most Damage”. Gartner Group. (November 2002)