Encryption
What is Encryption?
Encryption is a cryptographic technique that utilizes complex algorithms to convert plain text into ciphertext, rendering it indecipherable to unauthorized entities. The process involves using cryptographic keys, where the encrypted key transforms the data, and the corresponding decryption key restores it to its original form. The ciphertext remains incomprehensible without the decryption key.
Encryption is the most effective way to protect sensitive data at rest and in transit, but it is also the most complex to implement and manage. It reversibly allows authorized users to convert the ciphertext back to plaintext using the correct encryption key. The dual-key system ensures secure communication and storage of sensitive information and guards against data breaches and unauthorized access.
How Encryption Works?
It is a sophisticated process designed to secure sensitive information by transforming plain text into an unreadable form, known as ciphertext. Understanding its mechanics is crucial to appreciate its role in safeguarding data in various digital environments.
- Cryptographic keys: It relies on cryptographic keys, which include an encryption key and its corresponding decryption key. The former key transforms plain text into ciphertext, while the latter key reverses this process, restoring the original information.
- Algorithmic Complexity: Complex algorithms transform plain text into random and unintelligible arrangements of characters, enhancing data security. Reversing the process without keys becomes computationally infeasible for unauthorized entities due to the algorithm’s complexity.
- Symmetric and Asymmetric Encryption: Encryption can be symmetric or asymmetric. The former employs the same key for encryption and decryption, whereas the latter uses a public-private key pair. Symmetric encryption is efficient but requires secure key distribution, while asymmetric encryption offers better security but is computationally intensive.
- Reversibility and Decryption: Its reversibility features allow authorized users to use the correct decryption key to convert ciphertext back to plaintext. This reversible nature provides secure access to the original information, striking a delicate balance between data security and privacy for authorized data usage.
- Key Management: Though it is a powerful tool, its practical implementation necessitates robust key management. Safeguarding encrypted keys is crucial, as unauthorized access could compromise the entire masking process.
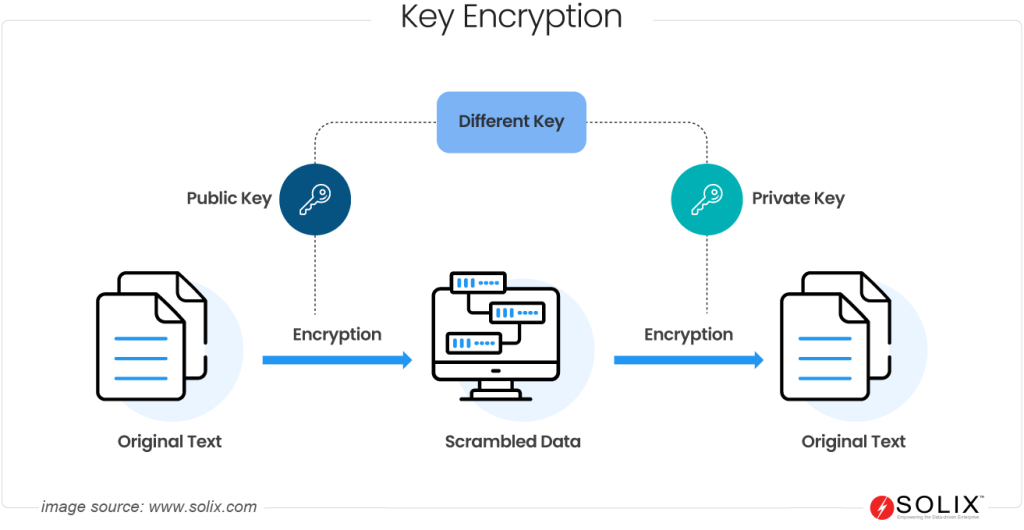
Pictorial representation of how Encryption works
Benefits of Encryption
It is the cornerstone of modern data security practices and offers many benefits, including safeguarding sensitive information and fortifying overall data protection strategies. Understanding the benefits is paramount to comprehending its vital role in securing digital assets.
- Confidentiality Assurance: It prevents unauthorized access by converting plain text into unreadable ciphertext, ensuring data confidentiality and mitigating the risk of data breaches.
- Compliance with Data Regulations: Encrypting data is crucial for compliance with data protection regulations like GDPR and PCI DSS. It aids in meeting legal requirements for safeguarding sensitive information such as PII, financial records, and health data.
- Secure Data Transmission: Encrypting data secures communication channels by masking sensitive information, crucial in digital transactions, online communications, and cloud-based services, where data traverses networks and the internet.
- Data at Rest Protection: It protects data at rest, including information on servers, databases, or storage devices. Encrypting such data ensures its incomprehensibility without the decryption key, even during unauthorized access.
- Threat Mitigation: Encrypting data is a potent deterrent against internal and external threats. It mitigates the risk of insider threats by limiting unauthorized access and fortifies defenses against external threats by rendering intercepted data indecipherable.
- Data Integrity: It contributes to maintaining data integrity. The reversible nature of this masking process ensures that authorized users, equipped with the correct decryption key, can access the original data without compromising its integrity.
- Flexibility: This versatile data masking technique is applicable in diverse environments, including production and non-production scenarios, as it supports dynamic and static data masking for comprehensive data security and privacy strategies.
Use Cases
It is a versatile and powerful sensitive data protection tool with extensive applications across diverse industries. It addresses unique challenges and ensures the confidentiality of sensitive information.
- Healthcare Data Protection: In healthcare, it acts as a shield by protecting patient records and sensitive health information. This ensures compliance with data privacy regulations and safeguards against unauthorized access to personal medical data.
- Financial Transactions and Banking: It is critical in securing financial transactions and banking operations. From online banking to digital transactions, It ensures the confidentiality and integrity of financial data, protecting users from fraud and identity theft.
- Production and Non-Production Environments: In the production environment, it secures customer data, protects intellectual property, and ensures compliance. In non-production, it masks sensitive data for testing, balancing security with development efficiency.
- Other fields: In e-commerce, it secures transactions and customer details, fostering trust. In human resources, government communications, and cloud computing, it safeguards employee data, ensures national security, and protects cloud-stored data.
In conclusion, Encryption stands as a foundational pillar in safeguarding digital information. Features like cryptographic keys and transformation processes ensure data confidentiality and integrity. Individuals and organizations can bolster their cybersecurity defenses by encrypting sensitive data, mitigating risks, and adhering to regulatory requirements.
FAQs
How does encryption differ from hashing or encoding?
Encryption involves converting data into a scrambled format using an algorithm and a key, which can be reversed with the decryption key. Hashing creates a fixed-size output that cannot be reversed, while encoding is reversible but not designed for security.
Can encrypted data still be intercepted or accessed without authorization?
Encrypted data can be intercepted, but without the decryption key, it remains unreadable and unusable to unauthorized parties. Robust encryption methods significantly reduce the likelihood of successful decryption without the key.
How does end-to-end encryption differ from standard encryption methods?
End-to-end encryption ensures that data remains encrypted from the sender to the recipient, with decryption only occurring at the endpoint. This differs from standard encryption, where intermediaries may decrypt and re-encrypt data along the transmission path.
Does encryption impact data processing speed or system performance?
Encryption can introduce overhead, impacting data processing speed and system performance, particularly with complex encryption algorithms or large datasets. However, modern encryption methods are optimized to minimize these effects.





