Incident Response
What is Incident Response?
Incident Response is the systematic approach to address and manage security breaches or cyberattacks. This proactive process includes preparation, detection and analysis, containment and eradication, recovery, and post-incident analysis. It’s a multi-step process that aims to minimize damage, limit disruption to operations, and restore normal functionality as quickly as possible.
Importance of Incident Response
Incident response is crucial for organizations due to several reasons:
- Minimizing Damage: Swift incident response helps minimize the impact of security breaches, reducing potential financial losses and operational disruptions.
- Protecting Data: Effective incident response safeguards sensitive data, ensuring compliance with regulations and customer trust.
- Maintaining Continuity: A well-executed incident response plan enables organizations to maintain business operations despite security incidents, ensuring continuity and resilience.
- Improving Security Posture: Post-incident analysis provides valuable insights for enhancing cybersecurity measures, strengthening defenses, and preventing future incidents.
- Preserving Reputation: A prompt and transparent response to security incidents helps maintain trust with customers, partners, and stakeholders, safeguarding the organization’s reputation.
Types of Security Incidents
Security incidents can vary in nature and severity, encompassing various threats and vulnerabilities. Here are a few examples of security incidents:
- Malware Infections: Malicious software (malware) infections such as viruses, trojans, ransomware, and spyware can compromise systems, steal data, or disrupt operations.
- Phishing Attacks: Phishing involves deceptive emails, messages, or websites that trick users into revealing sensitive information like login credentials, financial details, or personal data.
- Unauthorized Access: Unauthorized access occurs when attackers gain unauthorized entry to systems, networks, or accounts, exploiting vulnerabilities or using stolen credentials.
- DoS and DDoS Attacks: Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks aim to overwhelm servers, networks, or websites with a flood of traffic, rendering them inaccessible to legitimate users.
- Insider Threats: Insider threats involve malicious or negligent actions by employees, contractors, or partners, including data theft, sabotage, or unauthorized access.
- Social Engineering: Social engineering techniques manipulate individuals into divulging confidential information or performing actions that compromise security, often through persuasion, deception, or coercion.
- Web Application Attacks: Web application attacks target vulnerabilities in web applications or services, including SQL injection, cross-site scripting (XSS), and remote code execution, enabling attackers to gain unauthorized access or manipulate data.
- Misconfiguration: Security incidents may occur due to misconfigured systems, software, or network devices or by exploiting known vulnerabilities, allowing attackers to gain unauthorized access or cause disruptions.
- Data Leakage or Exfiltration: Data leakage involves the unauthorized transmission or disclosure of sensitive information, either intentionally or inadvertently, often resulting in financial, legal, or reputational consequences.
How to Create an Incident Response Plan?
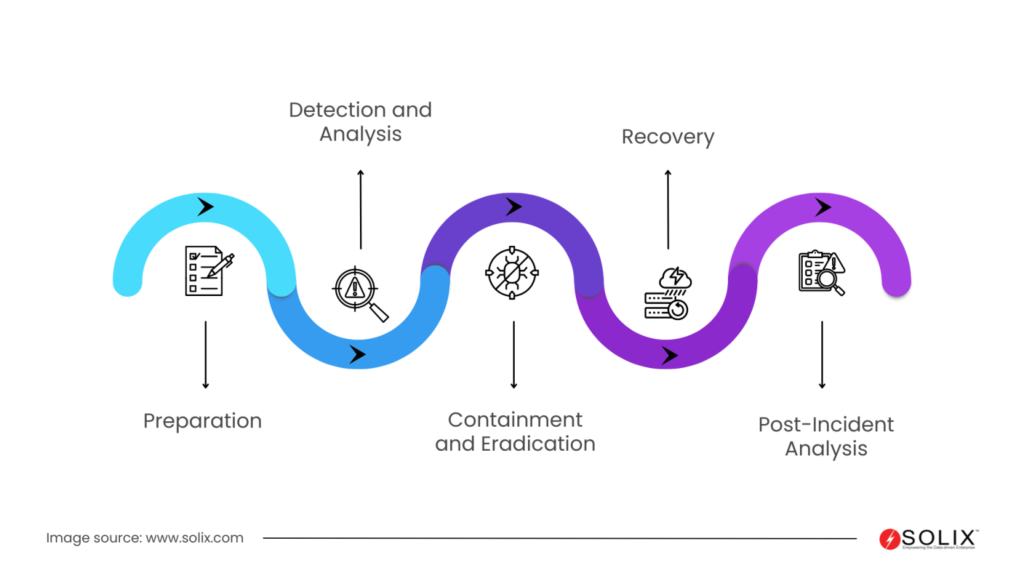
Creating an effective incident response plan involves several key steps. These steps ensure a comprehensive approach to managing security incidents. Here’s a structured guide to help you develop an incident response plan:
- Preparation: This phase involves proactively preparing for potential security incidents by developing comprehensive incident response plans, establishing communication channels, defining roles and responsibilities, conducting regular training and drills, and deploying essential tools and technologies to facilitate incident detection and response.
- Detection and Analysis: During this phase, Security teams continuously monitor systems, networks, and applications for unusual activity or security breaches. Detection mechanisms like intrusion detection systems (IDS), security information and event management (SIEM) systems, and endpoint detection and response (EDR) solutions are crucial for identifying potential security incidents.
- Containment and Eradication: Immediately after detecting a security incident, containment is crucial to prevent further damage. This involves isolating affected systems, deactivating compromised accounts, and implementing temporary security measures. Subsequently, the security teams focus on eradicating the root cause by closing backdoors or patching vulnerabilities.
- Recovery: After containing and eradicating the incident, the focus shifts towards restoring affected systems, data, and services to normal operations. This may involve restoring data from backups, applying security patches, reconfiguring systems, and conducting thorough testing to ensure the integrity and security of restored assets.
- Post-Incident Analysis: After resolving a security incident, conduct a comprehensive post-incident analysis. Identify the root causes. Assess the effectiveness of the response process. Gather lessons learned for future improvements. This analysis helps organizations enhance their incident response capabilities and strengthen their overall cybersecurity posture.
Cyber threats are becoming more sophisticated and widespread, making a robust incident response essential for all organizations. Understanding the components of incident response helps organizations prepare for security incidents effectively. Proactive preparation allows organizations to mitigate risks and respond confidently to breaches. This approach safeguards their assets, reputation, and business continuity.
FAQ
What role does employee training play in incident response?
Employee training is vital as it ensures staff know security protocols and recognize potential threats. Trained employees can report incidents efficiently, mitigating risks and minimizing security breach impacts. This boosts overall response effectiveness.
How often should incident response plans be tested and updated?
Breach response plans should be tested regularly, ideally through tabletop exercises or simulations, to ensure they remain effective and relevant. Additionally, plans should be updated whenever significant changes occur in the organization’s infrastructure, systems, or threat landscape.
What role does automation play in incident response?
Automation can streamline breach detection, analysis, and response processes, enabling faster response times and reducing manual workload. Automated tools quickly identify and contain security incidents. This lets humans focus on complex, decision-based tasks.