NIS 2 Directive
What is the NIS 2 Directive?
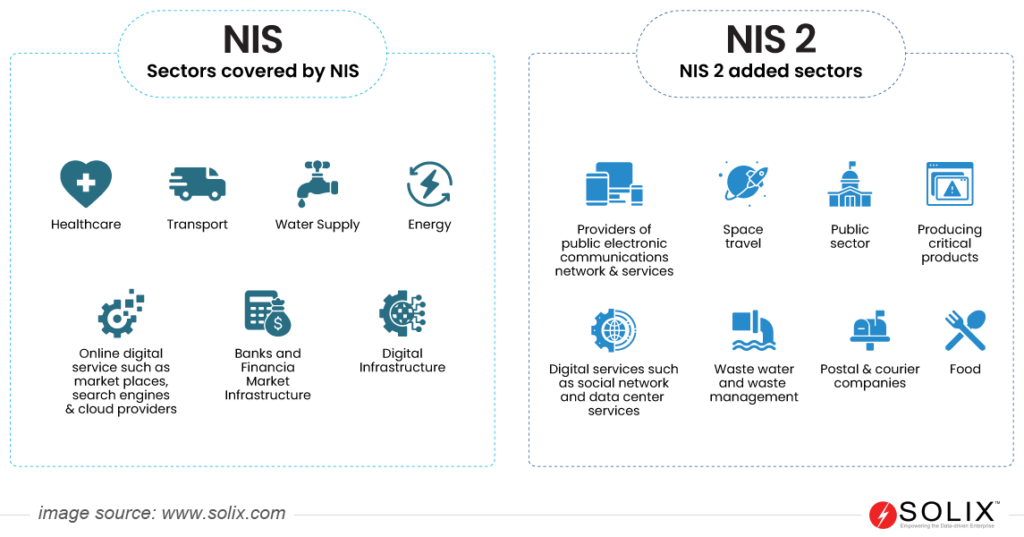
The NIS 2 (Network and Information Security) Directive is a piece of legislation enacted by the European Union (EU) in 2023. It is a revision of the NIS Directive 2016 and aims to tighten cybersecurity for critical energy, banking, and healthcare sectors. It expands the scope to include waste management, postal services, and essential product makers. This strengthens Europe’s collective defense against cyberattacks.
Overview of NIS 2 Directive
- Law: NIS 2 Directive
- Region: European Union
- Signed into Law: 16-01-2023
- Industry: Critical Infrastructure Sectors in EU
Personal Data Under The NIS 2 Directive
The NIS 2 Directive’s primary focus is cybersecurity, not data privacy. However, it does have some implications for personal data collected by entities in scope. The NIS 2 Directive emphasizes the principle of proportionality. This means organizations should only collect, store, and process personal data necessary for cybersecurity purposes and minimize the use of personal data when reporting incidents.
The Network and Information Security 2 Directive doesn’t replace the EU’s General Data Protection Regulation (GDPR), the primary legal framework governing personal data protection in the EU. Organizations subject to NIS 2 must also comply with the GDPR when handling personal data, ensuring its lawful collection, processing, and security.
Key Components of NIS 2 Directive
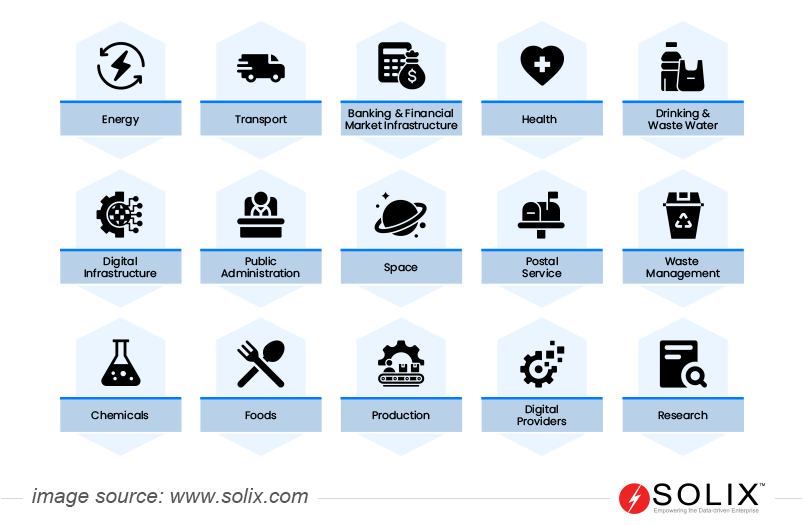
- Expanded Scope: NIS 2 extends its reach beyond critical infrastructure sectors like energy and transport to encompass essential services like waste management, postal services, and public administration. This broader scope reflects the increasingly interconnected nature of our digital world.
- Risk Management: Organizations must implement comprehensive risk management measures, including threat identification, vulnerability assessments, and incident response plans. Regular penetration testing and security audits are also mandated.
- Incident Reporting: Mandatory reporting of significant incidents within 24 hours ensures timely response and minimizes potential damage.
- Supply Chain Security: Measures to address risks posed by third-party vendors and suppliers are required, promoting robust security across the entire value chain.
- Information Sharing: Enhanced collaboration among member states and stakeholders allows for collective threat intelligence and improved incident response capabilities.
Data Protection Principles
Under the NIS 2 Directive, data protection is a fundamental principle emphasizing the confidentiality, integrity, and availability of information. Organizations must implement appropriate technical and organizational measures to safeguard PII against unauthorized access, disclosure, alteration, or destruction, aligning with the General Data Protection Regulation (GDPR) principles.
Rights Under NIS 2 Directive
- Right to be informed: Individuals can know if their data has been involved in a cybersecurity incident.
- Right to rectification: Individuals can request the correction of inaccurate or incomplete data.
- Right to restriction of processing: Individuals can request restrictions on processing their data.
Who Needs to Comply with the NIS 2 Directive?
Any organization operating within critical infrastructure or essential services sectors (operators of essential services – OES, and digital service providers – DSPs) defined by the directive must comply with NIS 2 requirements. Large and medium-sized companies within these sectors are also subject to the regulations.
- OES are organizations providing services crucial to society and the economy, regardless of size, like energy, transport, banking and finance, postal and courier services, waste management, water supply, healthcare, public administration, etc.
- Large and medium-sized companies have over 50 employees. They meet specific financial thresholds based on their sector. For energy, transport, waste management, postal, and public administration, the thresholds are €50 million annual turnover or €43 million balance sheet total. For healthcare and digital infrastructure sectors, the threshold is €10 million annual turnover.
Exceptions
- Micro and small enterprises: While encouraged to adopt appropriate cybersecurity measures, micro and small businesses within designated sectors are exempt from some specific requirements due to their limited resources.
- Non-profit organizations: Non-profit organizations delivering essential services fall under the scope of NIS 2, but specific considerations are made for their unique operating context.
Noncompliance Fines
- Essential Entities: Up to the greater of €10 million or 2% of their global annual turnover.
- Important Entities: Up to the greater of €7 million or 1.4% of their global annual turnover.
Adhering to the Network and Information Systems Directive 2 is vital for safeguarding critical infrastructure and digital services against evolving cyber threats. By embracing its key components, organizations fortify their cybersecurity posture, protect sensitive information, and mitigate risks. Implementing proactive data security solutions, like data masking, aids compliance with such regulations.
FAQs
What is the NIS 2 Directive, and to whom does it apply?
The Network and Information Systems Directive 2 is an EU legislation that enhances the cybersecurity resilience of critical infrastructure and digital service providers. It applies to operators of essential services and digital service providers across various sectors.
What sets apart the NIS 2 Directive from its predecessor?
The Directive broadens the scope of its predecessor to include more sectors and entities. It clarifies reporting obligations and sets stricter cybersecurity requirements. These measures address emerging threats and vulnerabilities.
What are the key requirements under the NIS 2 Directive?
The Directive requires essential service operators and digital service providers to implement robust cybersecurity measures. They must conduct risk assessments and establish incident response plans. They must also report significant cybersecurity incidents to relevant authorities.