On-the-Fly Data Masking
What is On-the-Fly Data Masking?
On-the-fly data Masking is a dynamic data protection approach involving real-time modification of sensitive information as it moves through different systems and processes. Unlike static data masking, which applies irreversible changes to the entire dataset, it allows organizations to mask data dynamically based on user privileges and contextual requirements.
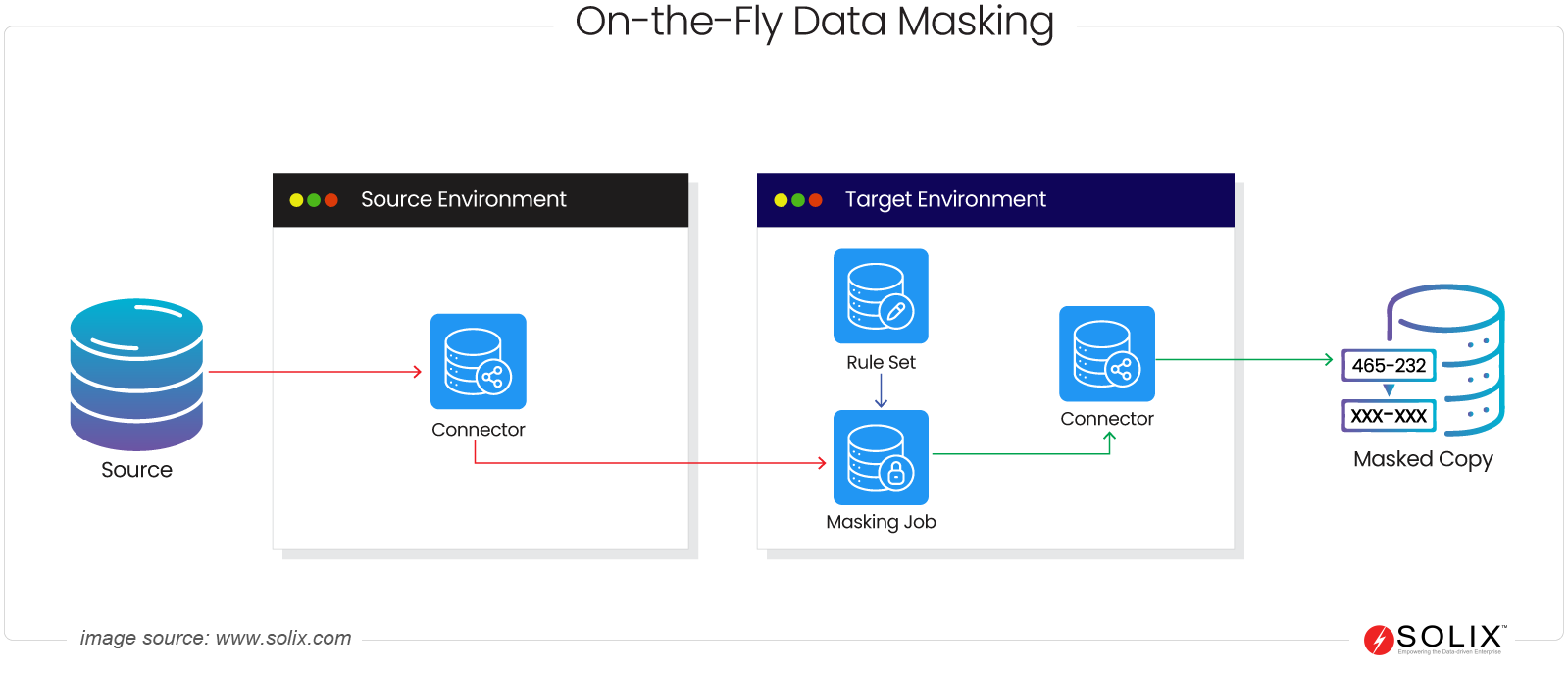
How On-the-Fly Data Masking Works?
This method involves intercepting data requests through different systems and applications, identifying sensitive data elements, and dynamically applying masking techniques to conceal or replace this information.
When a user requests access to data, the On-The-Fly Data Masking mechanism assesses the user’s permissions and the nature of the request. If the data contains sensitive information, the masking process triggers. Various masking techniques, including data anonymization, encryption, redaction, and others, are dynamically applied to ensure that sensitive information is concealed, altered, or substituted.
Difference between On-the-Fly and Dynamic Data Masking
| Feature | On-the-Fly Data Masking | Dynamic Data Masking |
|---|---|---|
| Timing | Real-time, during data access/transfer | On-demand, at query execution |
| Data Modification | Data is masked before it is presented to the user | Data presentation is masked in query results |
| Data Location | Masked data is stored in a separate target environment | Unmasked data remains in the original database |
Here are a few analogies to illustrate the difference.
Scenario 1: Magic Filter
On-the-fly data masking functions as an integral filter seamlessly incorporated into this pipeline. As the data moves through, the filter instantaneously masks sensitive details and stores the original data in the targeted database before presenting the masked data to the user. Dynamic masking filters only when a specific query is run on the database/filter and won’t store any copy anywhere.
Scenario 2: A chef with a secret recipe
The chef has two recipe books – one original and one with masked ingredients. When someone asks for the recipe with an on-the-fly query, the chef grabs the masked book and shows it. For dynamic masking, the chef has only one recipe book (the original). When someone asks for the recipe, the chef might cover up certain ingredients with his hand while showing them the rest.
Both scenarios present a masked recipe “in real-time” from the user’s perspective (the person asking for the recipe). However, masking occurs differently in this case, as it occurs on the fly with a separate masked copy and dynamically by manipulating the presentation at the time of request.
Benefits
- Real-time Protection: It immediately protects sensitive data as it is accessed, ensuring that unauthorized users only see masked or obfuscated information.
- Dynamic Adaptability: This approach allows for dynamic adjustments to masking rules. These adjustments are based on the user’s access permissions or specific data requests. This ensures sensitive information remains hidden. It provides access to non-sensitive data.
- Reduced Data Exposure: On-the-fly masking minimizes the risk of exposing sensitive information. It does this by dynamically masking data as it is accessed. This reduces the likelihood of data breaches or leaks.
- Improved Performance: It typically imposes minimal overhead on database performance since masking rules are applied dynamically during data retrieval rather than pre-processing the entire dataset.
- Simplified Implementation: Implementing on-the-fly masking can be simpler than static masking. This can lead to faster deployment and easier maintenance of masking policies.
- Enhanced Flexibility: It offers greater flexibility in managing access to sensitive data, as masking rules can be adjusted dynamically based on changing business requirements, compliance mandates, or security policies.
Use Cases
With its dynamic and real-time capabilities, on-the-fly masking is a versatile solution across various use cases, significantly contributing to data security and privacy.
- Non-Production Environments: It allows organizations to dynamically mask sensitive data, ensuring that the testing environment mirrors real-world scenarios without compromising the confidentiality of actual data.
- Analytical Environments: By dynamically masking data based on user roles and contextual requirements, analytics teams can work with accurate and representative data, fostering data-driven decision-making without compromising data privacy.
- Secure Data Sharing: It can address the complexities of different masking techniques. This ensures that only authorized individuals access specific details. It minimizes the risk of data exposure or misuse in collaborative projects.
- Data Privacy Regulations: On-the-fly masking provides a solution by dynamically adapting to changing data privacy requirements. This ensures that organizations can comply with evolving regulations without compromising operational efficiency.
- Dynamic Access Controls: The dynamic nature of access controls enhances security. It streamlines data access for various organizational stakeholders. This makes on-the-fly masking particularly effective. This is especially true in scenarios where dynamic access controls are critical.
In summary, On-The-Fly Data Masking integrates advanced techniques to address various use cases. It secures non-production environments and facilitates analytics. It enables secure data sharing and ensures compliance with data privacy regulations. Its adaptability and real-time capabilities make it a cornerstone in organizations’ efforts to fortify their data security and privacy strategies across diverse operational scenarios.
FAQs
How does On-the-Fly data masking handle unstructured data formats like text documents or images?
It employs advanced techniques. These include tokenization or encryption. It masks sensitive elements within unstructured data, such as text or images. It preserves data format while ensuring comprehensive protection.
How does On-the-Fly data masking handle complex data relationships and dependencies?
It utilizes sophisticated algorithms to manage intricate data relationships seamlessly. It ensures consistent masking across interconnected data elements, preserving integrity while concealing sensitive information.
Can On-the-Fly data masking support fine-grained access controls for different user roles or privileges?
Yes, On-the-Fly data masking offers fine-grained access controls, ensuring that users see only the data they’re authorized to access. It tailors masking policies based on user roles, maintaining confidentiality while allowing necessary access.





