Sensitive Information
What is Sensitive Information?
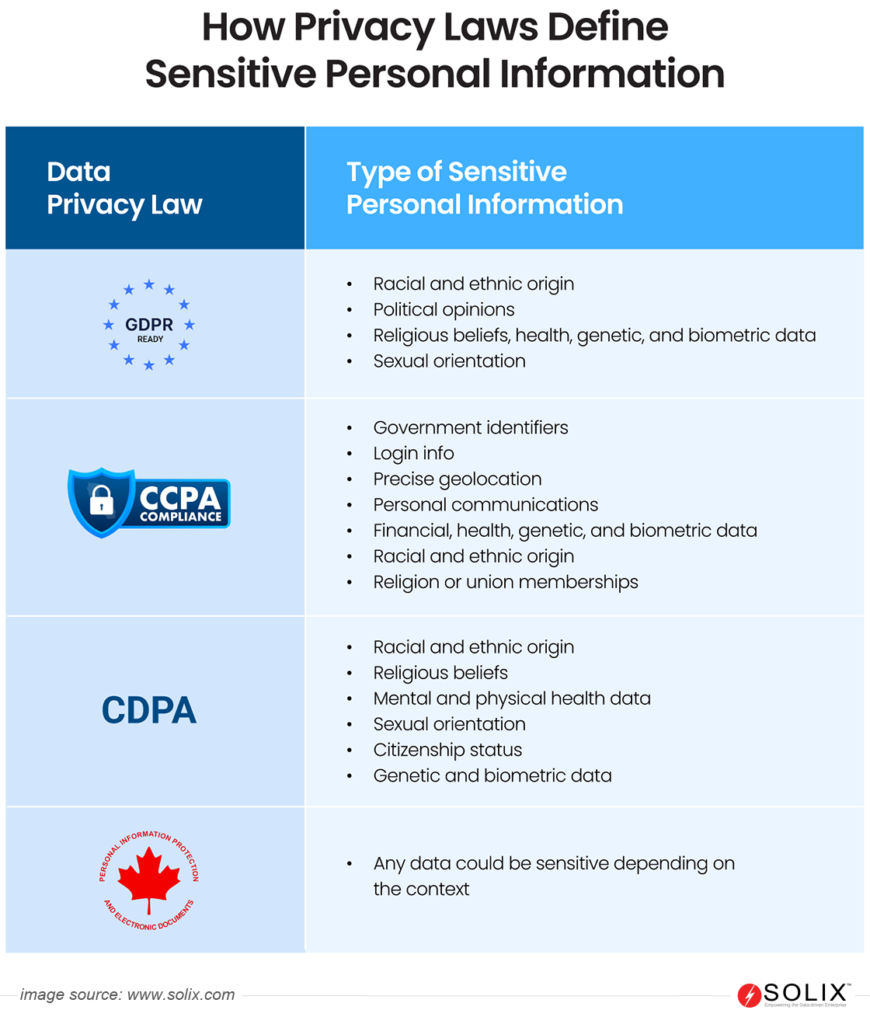
Sensitive Information is data that, if disclosed or accessed without proper authorization, could pose a risk to individuals, organizations, or both. This type of information is often subject to privacy and security regulations, and its exposure may result in financial, legal, or reputational consequences. Sensitive data can take various forms, encompassing personal, financial, or proprietary details.
Types of Sensitive Information
- Personally Identifiable Information (PII): PII includes any data that can be used to uniquely identify an individual. This may include names, addresses, social security numbers, passport numbers, etc.
- Financial Information: It encompasses details related to an individual’s or organization’s financial transactions, such as credit card numbers, bank account information, transfers, investments, or financial statements.
- Healthcare Data: Protected health information (PHI) includes medical records, health insurance details, or any other information related to an individual’s health or medical treatment.
- Legal and Compliance Data: Information related to legal matters, compliance documents, or contractual agreements falls into this category. Mishandling legal and compliance data can result in legal consequences, breach of contracts, and regulatory non-compliance.
- Educational Records: Educational data involves student information, such as name, date of birth, grades, transcripts, or disciplinary records. Unauthorized access to academic records can compromise student privacy and violate educational institutions’ policies.
- Government-Issued Identifiers: This includes data like social security numbers, passport numbers, or driver’s license information issued by government entities. Unauthorized access to these identifiers can lead to theft, financial fraud, or other malicious activities.
- Biometric Data: Biometric information includes fingerprints, retina scans, voice patterns, or any unique biological characteristics used for identification. Unauthorized access can compromise individual privacy and lead to identity theft.
- Employee Personnel Records: This includes information related to employees, such as salary details, performance reviews, or disciplinary records. Mishandling employee personnel records can lead to legal consequences, privacy violations, and damage to workplace trust.
- Login Credentials: Login credentials include usernames, passwords, PINs, or any authentication data used to access systems, applications, or accounts. Unauthorized access to login credentials can result in account takeovers, data breaches, and identity theft.
- Location Data: This includes information about an individual’s whereabouts obtained through GPS, mobile devices, or other tracking technologies. Unauthorized access to location data can compromise personal safety and privacy and lead to stalking or other malicious activities.
- Communication Content: This includes the content of emails, messages, or voice communications that may contain sensitive or confidential information.
- Consumer Purchase History: This includes details about an individual’s buying habits, product preferences, or transaction history. Unauthorized access can lead to targeted advertising, identity theft, or exploitation of consumer habits.
- Social Media Data: This includes information gathered from social media profiles, like personal details, posts, connections, and other information. Unauthorized access can lead to privacy violations, social engineering attacks, and identity theft.
- Supply Chain Information: This includes details about a company’s suppliers, vendors, or partners, including contracts, pricing, logistical information, billing, or anything else that should be confidential.
- Children’s Information: This includes data related to minors, such as their names, addresses, educational details, paternal details, or any other information that could be used for illegal aspects. Stringent regulations, like COPPA, mandate the protection of children’s information.
- Asset and Inventory Data: This includes information about an organization’s physical assets, including inventory levels, serial numbers, location details, etc. Unauthorized access can impact business operations, supply chain integrity, and competitiveness.
- Intellectual Property (IP) Documents: Intellectual Property (IP) documents include patents, trademarks, copyrights, or any information about an organization’s intellectual property. Unauthorized access can lead to IP theft, counterfeiting, and loss of competitive advantage.
- Trade Secrets: This includes proprietary information, such as manufacturing processes, formulas, or business strategies, that provides a competitive advantage. Unauthorized access can lead to loss of market advantage, decreased competitiveness, and legal ramifications.
- Criminal Records: This includes information about an individual’s criminal history, like arrests, convictions, and court records.
- Tax Identification Numbers (TIN): This includes unique numbers assigned for tax purposes, such as Social Security Numbers (SSN), Employer Identification Numbers (EIN), or anything similar.
- Corporate Financial Reports: This includes detailed financial statements, including income statements, balance sheets, cash flow statements, etc. Unauthorized access can lead to insider trading, corporate espionage, and reputational damage.
- Research and Development Data: This includes information on ongoing research, product development, innovation efforts, etc. Unauthorized access can compromise competitive advantage, delay product launches, and impact market positioning.
- Immigration Status Information: This includes data about an individual’s citizenship, residency status, or immigration documents. Unauthorized access can lead to discrimination, legal consequences, and potential threats to an individual’s safety.
- Emergency Contact Information: This includes details about individuals to be contacted in emergencies, including names, relationships, and contact numbers.
Political Affiliations: This includes information about an individual’s political beliefs, affiliations, or contributions. Mishandling can lead to privacy violations, discrimination, and potential threats to an individual’s safety. - Insurance Policy Details: This includes information related to insurance policies, including coverage details, beneficiaries, and premium payments.
- Visitor and Guest Logs: This includes records about individuals who have visited a facility or event. Unauthorized access can compromise security, lead to privacy violations, and pose risks to physical safety.
- Voice Recordings: Recorded voice conversations are often used in customer service or call center interactions. Unauthorized access can lead to privacy violations, reputational damage, and legal consequences.
- Client Communication: This includes Emails, messages, or documents exchanged with clients containing confidential business information. Unauthorized access can lead to data leaks, loss of client trust, and legal consequences.
- Software License Keys: This includes codes or keys granting access to and validating the use of software. Unauthorized access can lead to software piracy, financial losses, and compromised integrity.
Sensitive Information is valuable for individuals and organizations and a cornerstone of privacy, security, and ethical behavior. Recognizing its importance and implementing robust measures to protect it are essential for building trust, maintaining compliance, and fostering a secure and ethical environment. Remember, the proactive protection of Sensitive Information is not just about compliance; it’s a strategic move to build a resilient data infrastructure that withstands the challenges of an ever-evolving digital landscape.
FAQs
What constitutes sensitive information?
Sensitive information includes data that, if compromised, could lead to financial, reputational, or personal harm. This encompasses personally identifiable information (PII), financial data, health records, intellectual property, and any data subject to regulatory protection or confidentiality obligations.
How do organizations determine what qualifies as sensitive information?
Organizations typically assess sensitivity based on legal requirements, industry standards, potential impact on individuals or the organization, and contextual considerations. This involves evaluating the nature of the data, its intended use, and the potential consequences of unauthorized disclosure.
Can sensitive information vary across different industries and regions?
Yes, the definition of sensitive information can vary significantly depending on industry-specific regulations, cultural norms, and regional privacy laws. For example, healthcare organizations may consider medical records highly sensitive, while financial institutions prioritize protecting financial transaction data.
How do emerging technologies impact the handling of sensitive information?
Emerging technologies such as artificial intelligence, cloud computing, the Internet of Things (IoT), and blockchain introduce new opportunities and challenges in managing sensitive information. While they offer enhanced data processing and analysis capabilities, they also require robust security measures to protect against potential threats and vulnerabilities.